Zoom, the videoconferencing software that has recently skyrocketed in popularity due to the remote work requirement brought about by the coronavirus pandemic, is currently plagued with lots of security issues.
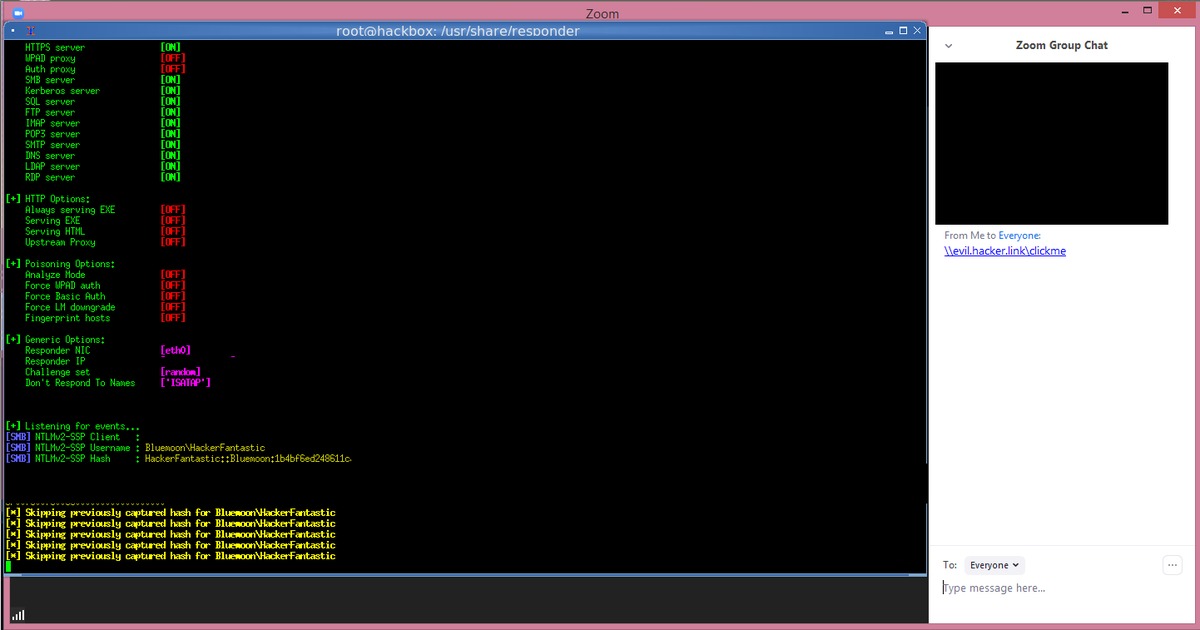
According to reports from several security researchers on the Internet, there’s a newly found vulnerability in Zoom that allows an attacker to steal Windows login credentials from other users. The problem stems from the fact that Zoom’s chat handles links inappropriately by converting Windows networking UNC (Universal Naming Convention) paths into clickable links. When a user clicks on such a link, Windows will leak the user’s Windows login name and password. Even though the passwords are hashed, this is still considered inappropriate application behaviour as hashed passwords are susceptible to compromise using the right tools.
This vulnerability was first found by security researcher @_g0dmode and verified by security researcher Matthew Hickey. Additionally, Hickey told the news outlet that this vulnerability can be used to launch programs on a victim’s computer when they click on a link, though Windows will (by default) at least give a security warning before launching the program.
In order to ensure you’re secure as a windows user, before Zoom issues a fix, press Windows+R to open Run, type mmc in the empty box and tap OK , choose Add/Remove a Snap-in, click Add then select Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers and set to “Deny all”.
Aside from the current issue, it has also recently been discovered that that Zoom doesn’t actually use an end-to-end encrypted connection for its calls, despite claiming to do so. Additionally, the app has also been alleged to leak users’ emails and photos to unrelated parties.
As if we’ve not had enough, Zoom software allegedly has some worrying features pertaining to privacy. As with any other issues, hackers hackers have recently been discovered to be leveraging the app’s newfound popularity to trick users into downloading malware